Since late December 2018, Electrum Bitcoin wallet users have been plagued by targeted phishing attacks, resulting in a staggering loss of 771 BTC (equivalent to roughly $4 million). Research from Malwarebytes Labs revealed a cunning scheme where unsuspecting users were tricked into downloading a malicious version of the wallet, exploiting a vulnerability within the software.
In a surprising turn of events, the developers behind Electrum chose to leverage the same flaw in February. Their aim? To redirect users towards downloading the latest patched version of the wallet. However, the situation escalated further in March as developers began exploiting another, undisclosed vulnerability. This maneuver, described as a “counter-attack,” effectively prevented vulnerable clients from connecting to malicious nodes.
Adding to the turmoil, a botnet initiated distributed denial-of-service (DDoS) attacks targeting Electrum servers. This malicious tactic aimed to exacerbate the situation by specifically targeting users who were still operating with outdated and vulnerable versions of the wallet, further increasing their risk of falling victim to the phishing attacks.
Why Hackers Targeted Electrum
Electrum, known as a “lightweight” Bitcoin wallet, utilizes a modified version of a technique called ‘Simplified Payment Verification’ (SPV), as explained by Malwarebytes researchers. This approach allows users to conduct transactions without the burden of downloading the entire Bitcoin blockchain, which can reach hundreds of gigabytes in size. Instead, Electrum operates on a client/server model. The wallet, acting as the client, is programmed to connect to a network of peers by default to validate transactions.
While this method has generally been considered secure, it has become a target for attackers due to the open nature of the Electrum network, where anyone can operate a public Electrum peer. This vulnerability has been increasingly exploited, as evidenced by the significant rise in the number of active peers within the Electrum network, as shown in the graph below.

Malicious wallets
Malwarebytes researchers categorized the malicious Electrum wallets into two distinct types: “Variant 1” and “Variant 2”. Their investigation revealed that the individuals or groups behind this campaign have been active for a significant period, suggesting the possibility of other malware variations existing prior to December 21, 2018.
Several key differences in the malware indicate that Variants 1 and 2 are likely operated by separate entities. Variant 1 stands out due to a unique function that uploads stolen wallet keys and seed data to a remote server. The attackers went to considerable lengths to conceal this function, obfuscating the data exfiltration code within a file named “initmodules.py,” which is not typically found in Electrum wallets. Additionally, any funds discovered within the compromised wallet were transferred to one of several pre-programmed public addresses under the scammers’ control. The specific destination address for the stolen funds was determined by the address format used by the infected user’s Electrum wallet.
Researchers observed that Pay-to-PubkeyHash (P2PKH) addresses were the default setting during wallet setup, implying that users who retained the default settings were most susceptible to the attack. This conclusion is supported by analyzing the activity within the following addresses:

The evidence suggests a deep understanding of Electrum and its codebase on the part of the attackers. They implemented several modifications, including disabling auto-updates, removing confirmation prompts like “Yes, I am sure,” and even eliminating the ability to perform Replace-by-Fee (RBF) transactions. RBF is a feature added to the Bitcoin codebase later in its development, allowing users to create a double-spend transaction.
In this context, a user familiar with RBF could potentially reverse the stolen funds transfer by double-spending the input with a higher fee. However, the attackers’ actions effectively neutralized this possibility for most users, as awareness of RBF functionality remains limited.
Tracing the Stolen Bitcoins
A crucial question remains: where did all the stolen Bitcoin end up?
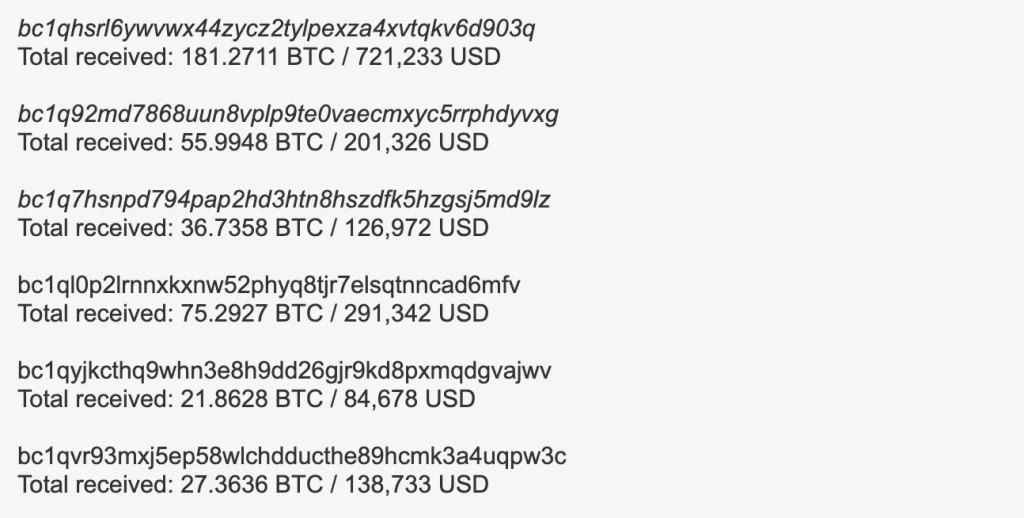
Analysis of blockchain transactions revealed that the funds stolen by Variant 1 were systematically broken down into smaller amounts.
Specifically, 48.36 BTC (equivalent to $244,001) was primarily regrouped into 3.5 BTC ($17,659) and 1.9 BTC ($9,586) increments. Researchers suspect this pattern is indicative of a money laundering technique known as “smurfing.“
This method involves dividing large sums of money into smaller deposits, typically below a certain threshold (in this case, $7,000), to avoid triggering a Currency Transaction Report (CTR) which is mandatory for transactions exceeding $10,000.
The Threat of Future Attacks
Malwarebytes researchers express significant concern regarding the potential for future attacks. In a blog post, they stated, “Anyone keeping track of cryptocurrencies knows they’re in for a wild ride. Determined threat actors exploited a vulnerability in the most popular Bitcoin wallet to create a very clever phishing attack that was able to net them at least over 3 million dollars in only a few months.”
The researchers further highlighted the retaliatory DDoS attacks launched by the criminals after Electrum took steps to protect users. They noted, “There most likely was some animosity between the two parties, but as the botnet continues to disable legitimate Electrum nodes, rogue ones get promoted to continue the vicious cycle of pushing the fake update and rob more victims of their cryptocurrencies.”
To mitigate these threats, individuals running their own Electrum servers are advised to take several precautions. Updating their wallet to the latest version (3.3.4) from the official repository is crucial. Additionally, users should remain vigilant and exercise caution when encountering warning messages, as these could be disguised phishing attempts. The battle against these cybercriminals and their evolving tactics is likely to continue, demanding ongoing vigilance and proactive security measures from both Electrum and its users.